A Targeted Approach for Building a Secure Air-Gapped System
Keywords:
Security, cyber security, information transfer, air gap, penetrationAbstract
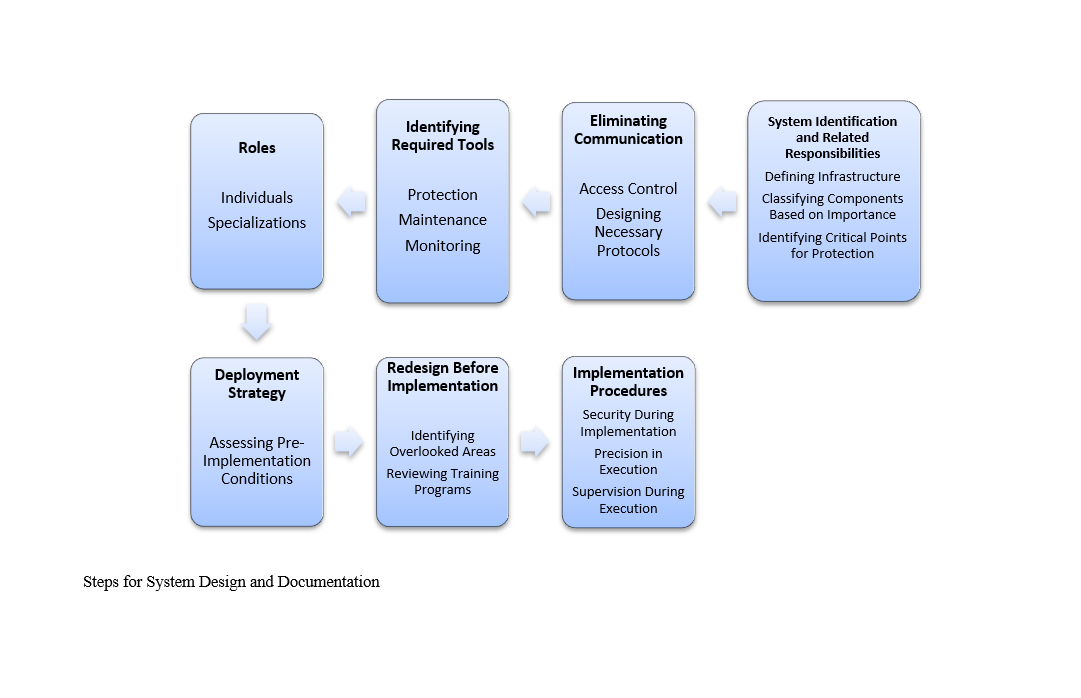
This study aims to present a targeted strategy for developing a methodology that leads to the design and implementation of an air-gapped system. The research integrates existing technologies from the fields of physics, cybersecurity, data transmission, physical protection, cryptography, and encoding. This paper is based on studies conducted on attacks targeting air-gapped systems, identifying vulnerabilities in each system, and subsequently proposing a solution. To achieve this, over 150 reputable global research articles were reviewed. In air-gapped systems, networked computer communications—whether wired or wireless—between the internal and external environments do not exist. As a result, these systems offer a higher level of security. However, studies indicate that they may still be vulnerable. This paper attempts to introduce a method that results in the creation of a structured list of tasks. Following this list aligns with organizational objectives for establishing an air-gapped system and ultimately leads to the design and implementation of such a system.
References
C. Heath-Kelly and Š. Shanaáh, "The long history of prevention: Social Defence, security and anticipat ing future crimes in the era of ‘penal welfarism’," (in en), Theoretical Criminology, vol. 26, no. 3, pp. 357-376, 2022/8// 2022, doi: 10.1177/13624806211056313.
A. E. Hassanien, M. Elhoseny, and SpringerLink, Cybersecurity and Secure Information Systems Challenges and Solutions in Smart Environments. (in English), 2019.
H. E. Amin, "An Integrated Approach to Cyber Risk Management With Cyber Threat Intelligence Framework to Secure Critical Infrastructure," Journal of Cybersecurity and Privacy, vol. 4, no. 2, pp. 357-381, 2024, doi: 10.3390/jcp4020018.
O. O. Amoo, "GDPR's Impact on Cybersecurity: A Review Focusing on USA and European Practices," International Journal of Science and Research Archive, vol. 11, no. 1, pp. 1338-1347, 2024, doi: 10.30574/ijsra.2024.11.1.0220.
M. Sauter, From GSM to LTE-Advanced Pro and 5G: an introduction to mobile network s and mobile broadband, Fourth edition ed. Hoboken, NJ: Wiley, 2021, p. 1.
Z. A. Genç, G. Lenzini, and D. Sgandurra, "Cut-and-Mouse and Ghost Control: Exploiting Antivirus Software with Sy nthesized Inputs," (in en), Digital Threats: Research and Practice, vol. 2, no. 1, pp. 1-23, 2021/3/31/ 2021, doi: 10.1145/3431286.
P. Katrakazas, "A Stakeholder Needs Analysis in Cybersecurity: A Systemic Approach to Enhancing Digital Infrastructure Resilience," Businesses, vol. 4, no. 2, pp. 225-240, 2024, doi: 10.3390/businesses4020015.
O. C. Obi, "Comprehensive Review on Cybersecurity: Modern Threats and Advanced Defense Strategies," Computer Science & It Research Journal, vol. 5, no. 2, pp. 293-310, 2024, doi: 10.51594/csitrj.v5i2.758.
E. S. Okafor, "Cybersecurity Analytics in Protecting Satellite Telecommunications Networks: A Conceptual Development of Current Trends, Challenges, and Strategic Responses," International Journal of Applied Research in Social Sciences, vol. 6, no. 3, pp. 254-266, 2024, doi: 10.51594/ijarss.v6i3.854.
M. Guri, "AiR-ViBeR: Exfiltrating Data from Air-Gapped Computers via Covert Surf ace ViBrAtIoNs," arXiv:2004.06195 [cs], 2020/4/13/ 2020. [Online]. Available: http://arxiv.org/abs/2004.06195.
M. Guri, Y. Solewicz, A. Daidakulov, and Y. Elovici, "Fansmitter: Acoustic data exfiltration from (speakerless) air-gapped c omputers," arXiv preprint arXiv:1606.05915, 2016 2016.
M. Guri, Y. Solewicz, A. Daidakulov, and Y. Elovici, "DiskFiltration: Data Exfiltration from Speakerless Air-Gapped Computer s via Covert Hard Drive Noise," arXiv preprint arXiv:1608.03431, 2016 2016.
E. Byres, "The air gap: SCADA's enduring security myth," (in en), Communications of the ACM, vol. 56, no. 8, pp. 29-31, 2013/8// 2013, doi: 10.1145/2492007.2492018.
D. Dumitriu and M. A.-M. Popescu, "Enterprise Architecture Framework Design in IT Management," (in en), Procedia Manufacturing, vol. 46, pp. 932-940, 2020 2020, doi: 10.1016/j.promfg.2020.05.011.
M. Guri, Y. Solewicz, and Y. Elovici, "Fansmitter: Acoustic data exfiltration from air-Gapped computers via f ans noise," (in en), Computers & Security, vol. 91, p. 101721, 2020/4// 2020, doi: 10.1016/j.cose.2020.101721.
M. Guri, B. Zadov, and Y. Elovici, "ODINI: Escaping Sensitive Data From Faraday-Caged, Air-Gapped Computer s via Magnetic Fields," IEEE Transactions on Information Forensics and Security, vol. 15, pp. 1190-1203, 2020 2020, doi: 10.1109/TIFS.2019.2938404.
M. Hanspach and M. Goetz, "On Covert Acoustical Mesh Networks in Air," arXiv:1406.1213 [cs], 2014/6/4/ 2014. [Online]. Available: http://arxiv.org/abs/1406.1213.
Q. Shan et al., "Estimation of Impulsive Noise in an Electricity Substation," IEEE Transactions on Electromagnetic Compatibility, vol. 53, no. 3, pp. 653-663, 2011/8// 2011, doi: 10.1109/TEMC.2010.2092782.
J. Szefer, "Survey of Microarchitectural Side and Covert Channels, Attacks, and De fenses," (in en), Journal of Hardware and Systems Security, vol. 3, no. 3, pp. 219-234, 2019/9// 2019, doi: 10.1007/s41635-018-0046-1.
I. Hwang, J. Cho, and S. Oh, "VibeComm: Radio-Free Wireless Communication for Smart Devices Using Vi bration," (in en), Sensors, vol. 14, no. 11, pp. 21151-21173, 2014/11/10/ 2014, doi: 10.3390/s141121151.
N. Mims, "Cyber-Attack Process," in Computer and Information Security Handbook: Elsevier, 2017, pp. 1105-1116.
H. Nyholm et al., "The Evolution of Volatile Memory Forensics," (in en), Journal of Cybersecurity and Privacy, vol. 2, no. 3, pp. 556-572, 2022/7/20/ 2022, doi: 10.3390/jcp2030028.
M. Guri, "Optical air-gap exfiltration attack via invisible images," Journal of Information Security and Applications, vol. 46, pp. 222-230, 2019 2019.
S. Sarkar, A. Chakraborty, A. Saha, A. Bannerjee, and A. Bose, "Securing Air-Gapped Systems," in Proceedings of International Ethical Hacking Conference 2019, vol. 1065, M. Chakraborty, S. Chakrabarti, and V. E. Balas Eds. Singapore: Springer Singapore, 2020, pp. 229-238.
F. A. Aboaoja, A. Zainal, F. A. Ghaleb, B. A. S. Al-rimy, T. A. E. Eisa, and A. A. H. Elnour, "Malware Detection Issues, Challenges, and Future Directions: A Survey," (in en), Applied Sciences, vol. 12, no. 17, p. 8482, 2022/8/25/ 2022, doi: 10.3390/app12178482.
J.-P. Aumasson and M. D. Green, Serious cryptography: a practical introduction to modern encryption. San Francisco: No Starch Press, 2017, p. 282.
Downloads
Published
Submitted
Revised
Accepted
Issue
Section
License
Copyright (c) 2025 Management Strategies and Engineering Sciences

This work is licensed under a Creative Commons Attribution-NonCommercial 4.0 International License.











